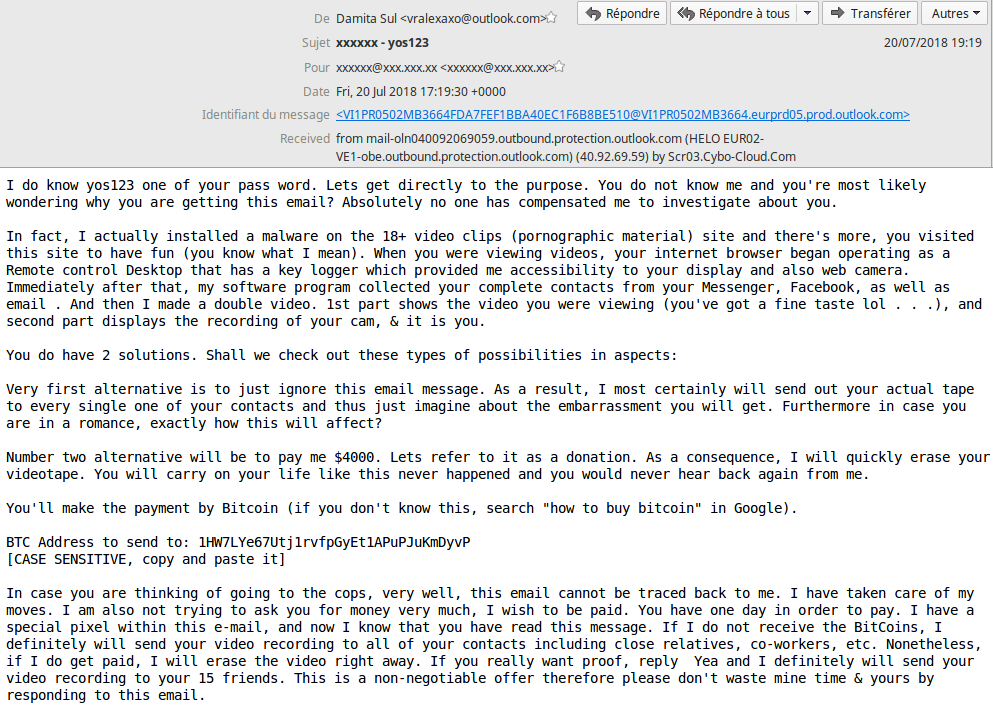
Publish Date: 17 septembre We spotted another spam campaign where the emails try to extort money from the recipient.
- cara wd btc miner.
- buy bitcoin with debit card usa.
- bitcoin sample wallet address;
The spammed message tries to induce fear by convincing users that their information is in the possession of the sender. The body of the email indicates that user's computer has been loaded with a remote access trojan RAT or that a pornography site the user has purportedly visited has a virus in it.
The cybercriminals will then demand payment, via Bitcoin, in exchange for the information on the user.
Interestingly, the emails arrive in different languages, depending on the recipient. In the next part of the manuscript, we show that the proposed separation principles can be extended also to a processor-coprocessor architecture. We propose a secure crypto-coprocessor, which can be used in conjunction with any general-purpose processor.
In the following part of the work, we examine the resistance of the HCrypt cryptoprocessor to differential power analysis DPA attacks. Following this analysis, we modify the architecture of the HCrypt processor in order to simplify its protection against side channel attacks SCA and fault injection attacks FIA.
Next, we study possibilities of dynamically reconfiguring selected parts of the processor - crypto-coprocessor architecture.
Campagnes d’hameçonnage en cours
The dynamic reconfiguration feature can be very useful when the cipher algorithm or its implementation must be changed in response to appearance of some vulnerability. Finally, the last part of the manuscript is dedicated to thorough testing and optimizations of both versions of the HCrypt crypto-processor.
Architectures of crypto-processors and crypto-coprocessors are often vulnerable to software attacks targeting the disclosure of encryption keys.
Separation rules are implemented on novel HCrypt crypto-processor resistant to software attacks targetting the disclosure of encryption keys. Keywords : Secure reconfiguration Separation rules Secure key management Secure crypto-coprocessor Secure crypto-processor. Document type : Theses.
Blackmail Scam Demands Payment in Cryptocurrency
Complete list of metadata Display. Cited literature [ references] Display Hide Download. Identifiers HAL Id : tel, version 1. Citation Lubos Gaspar. Other [cond-mat.