TOR makes it difficult for law enforcement authorities to locate ransom websites and shut them down.
How to trace ransomware payments end-to-end
As a result, it is no longer possible to rely on one of the most effective tactics against botnets: shutting down the control site. TOR also makes it harder to crawl the sites to get ransom wallet addresses, as the sites require that the crawler supports the TOR protocol.
The first phase of our research involved creating a corpus of ransomware binaries for all the major ransomware families. The key difficulty of that phase was to find which of the malicious binaries collected by VirusTotal belonged to a given family. To find these needles in the haystack we wrote rules that matched each variant of each ransomware family. This was a titanesque task as there were 34 families as shown in the tag cloud above and hundreds of variants.
These rules allowed us to collect an initial dataset of around Armed with our initial dataset, we turned to clustering and code similarity to find additional ransomware binaries automatically. This phase was essential because we knew that our rules, while very precise, missed a lot of ransomware binaries.
Ransom payments in realtime
As shown in the diagram above, the code similarity analysis helped find more ransomware, whereas the clustering algorithm that looked variously at the domain contacted, the files dropped, and other dynamic execution indicators, allowed us to assign the newly discovered ransomware to its correct family and variants. This phase allowed us to almost double the size of our dataset by uncovering an additional , binaries. Adding all those extra binaries ensured good coverage, and that our dataset was representative of ransomware activities. Once we had the bitcoin address associated with the ransomware binaries, the final step in closing the loop was to trace the payments through the bitcoin chain, to find out where the money was flowing and was cashed out.
Tracing bitcoin movements, while difficult, is possible. Bitcoin transactions are public and include all the information we need to trace ransom payments, as long as we know which wallets to look at. The screenshot above shows two transactions in this wallet. Each transaction contains the following information: the amount transferred, the sender wallet, the recipient wallet, and the date of the transaction.
The difficulty in tracing ransom payments through the blockchain is that you have to identify which wallets were used to pay the ransom and which wallets are used to cash out. The ransom wallets were identified by completing the first three phases of our research.
How to trace ransomware payments end-to-end
Combining these two datasets of wallets with bitcoin transaction records allowed us to attribute the transactions above to a ransom payment for the Locky ransomware family that was made in August We are also able to infer that the ransom amount of four bitcoins was bought on localbitcoins. In most cases, tracing payment is not that easy as cybercriminals move the bitcoins through multiple wallets in an attempt to evade payment tracing. Some use bitcoin mixers to make it even harder to trace the payments. However, this is not insurmountable, because no matter how many times the bitcoins are moved, ultimately they must be cashed out at exchange points.
So we just need to keep tracing movements until we reach a cash-out wallet. Bitcoin is anonymous if used perfectly. Luckily, no one is perfect. Even hackers make mistakes. It only takes one mistake to link stolen bitcoin to a hacker's their real identity. If you or your organization have been hit by ransomware, file a report. You can then monitor bitcoin addresses reported by you and by others.
Thanks for making the Internet a safer place!
Bitcoin Abuse Database
Do not pay ransoms. More information ». Bitcoin Abuse Database Tracking bitcoin addresses used by ransomware, blackmailers, fraudsters, etc.
It will also tweet the total amount the wallets have received every couple of hours. Below are more details on the three bitcoin wallets.
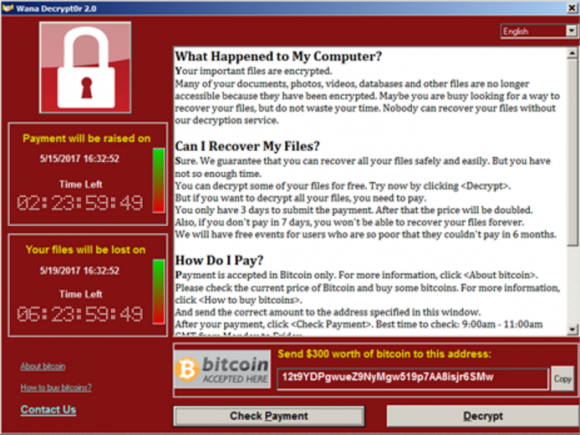
This wallet has received 38 payments totaling 6. You can view all of its transactions here. This wallet has received 35 payments totaling 5.
- computer bitcoin wallet.
- bitcoins total value?
- capital gains bitcoin usa.
- Watch as these bitcoin wallets receive ransomware payments from the ongoing global cyberattack?
This wallet has received 30 payments totaling 3. This article was updated with new numbers and details on May 13 at p.